Monitor Attacks In SEIM
The project features a PowerShell script that identifies and maps the geographic locations of failed RDP attack attempts using Azure Sentinel and a live honeypot VM, providing real-time cyber threat visualization.

Configured a virtual machine with intentionally weak firewall settings to permit inbound traffic. It’s vulnerable so hackers can attack it.
— THIS IS A HONEYPOT
Utilized Azure to set up the VM with all firewall ports open and configured settings to collect and log all events.

LIVE INBOUND TRAFFIC
Demonstration videos showcasing live RDP brute force traffic in the FireShell ISE and a simulated failed login attempt, with real-time reporting to Azure Log Analytics Workspace.

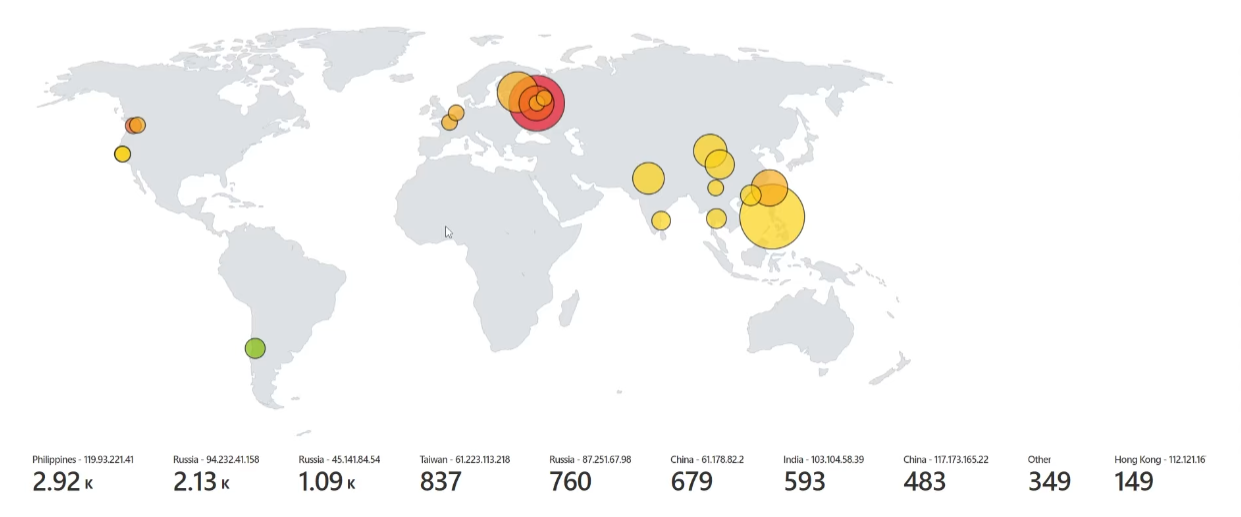
Wrote code to create a query that transforms raw data into a table, and then displayed it on a map.

WORLD MAP OF INCOMING ATTACKS AFTER 24 HOURS
Check out my Github for full source code